

Data records indexed across our distributed intelligence network, empowering next-generation investigations, real-time breach detection, and AI-driven cyber defense automation.
Built and refined over years of R&D, NiamonX integrates big data analytics, AI reasoning, and security intelligence into a single ecosystem — designed for individuals, enterprises, and security researchers worldwide.
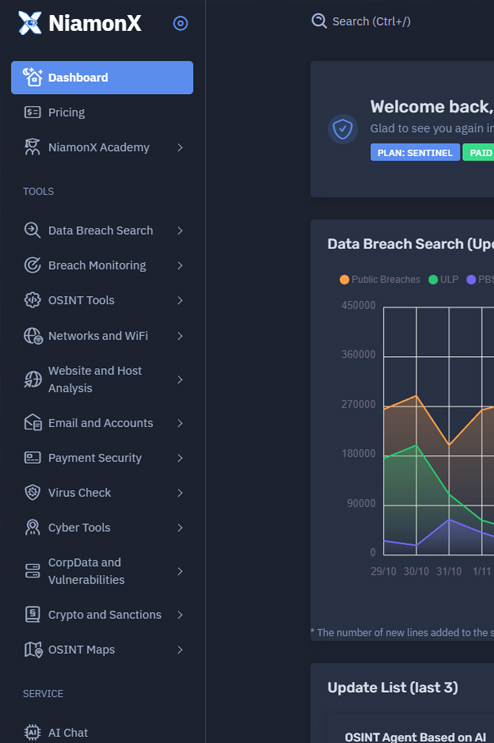
Each tool and service within the NiamonX Intelligence Network is built for deep analysis, automation, and actionable threat detection — enabling professionals to investigate faster, smarter, and more securely.

NiamonX is an independent AI & Cybersecurity company building the next generation of data-driven intelligence. Our system unites 196B+ breach records, 400+ distributed search nodes, and proprietary AI models into a single, high-performance infrastructure — empowering real-time investigations, threat detection, and digital forensics. We transform fragmented information from leaks, dark web, and open sources into clear, actionable intelligence.
Built through years of innovation and large-scale infrastructure work, NiamonX combines deep technical expertise in AI, data analysis, and cybersecurity engineering.
Our network indexes hundreds of billions of data points from breaches, corporate records, and darknets — providing unmatched visibility for analysts, businesses, and security teams.
Our proprietary AI models power real-time vulnerability scanning, phishing detection, and intelligent entity correlation — turning complex data into precise insights for proactive defense.
With zero-logging infrastructure and private cloud architecture, NiamonX ensures full confidentiality of user queries while automating threat analysis and OSINT workflows at scale.
A private, zero-log AI chat environment that lets you compare and interact with 10+ powerful language models — without limits. Discuss cybersecurity, analyze vulnerabilities, and explore real-time threat intelligence with total data anonymity. The only boundary is your plan's token capacity.
A premium tool for NiamonX subscribers. Explore a constantly updated database of publicly available Wi-Fi access points with known vulnerabilities. The data is collected and verified by the global InfoSec community. If your network appears on the map, immediately update your router credentials to maintain security.
VaultWarden is a self-hosted, zero-knowledge password manager built with military-grade end-to-end encryption. All cryptographic operations occur locally using Argon2 and AES-GCM standards. The server stores only encrypted blobs — without your master password, your data is mathematically unrecoverable.
Generate temporary, disposable email addresses instantly. Receive, read, and test messages in a secure sandboxed environment to protect your real inbox from spam, phishing, and tracking. Ideal for QA testing, web automation, and privacy-focused users.
An advanced intelligence system powered by NiamonX infrastructure. The OSINT AI Agent combines 14+ internal data sources with proprietary language models trained for context extraction, data correlation, and tool selection. It autonomously performs security audits and generates actionable OSINT reports. Currently in early deployment, it will soon integrate with all 66+ NiamonX tools.
The internal Academy and Learning System with practical modules, lectures, tests, and final exams. Upon completion, each participant receives a lifetime digital certificate verifiable through our online service. Courses cover Information Security, AI applications, Digital Hygiene, Programming Languages, Web Development, Network Administration, and Graphic Design — helping you gain real, hands-on expertise in cybersecurity and modern technologies.
A growing suite of advanced OSINT and cybersecurity tools — continuously improved, expanded, and powered by AI. New modules, data sources, and automation features are added regularly to help you stay ahead of emerging digital threats.
Powered by our internal services and intelligence tools, OSINT Agent AI interprets complex technical data in a clear, human-friendly way — providing concise, AI-driven explanations with smart compression and contextual understanding.

Our solutions integrate seamlessly with your existing systems.

From planning and development to integration and optimization.
Continuous scanning of leaked records, giving users access to actionable intelligence for OSINT investigations.
read moreOver 10 specialized AI models for vulnerability analysis, OSINT auditing, and automated cybersecurity insights.
read moreContinuous monitoring of personal and corporate data leaks with instant alerts for detected breaches.
read moreA comprehensive suite of over 66 specialized OSINT tools, enabling search across leaks, social media, domains, and IPs with AI-powered analysis.
read moreOur search robot continuously monitors infostealers and dark web leaks, providing real-time alerts and AI-driven analysis of compromised data.
read moreOver 64,500,000 WiFi access points mapped worldwide, including passwords, MAC addresses, and geolocation data, with full search and API support.
read moreAll authorization is handled through Zitadel IAM over encrypted channels hosted in Reykjavík, Iceland. Data is protected using AES-256-GCM within the ZITADEL Storage Encryption Layer, securing passwords (bcrypt or Argon2id), refresh and ID tokens, private keys, and OAuth credentials. Strict password rotation and enforced 2FA policies prevent credential compromise. In case of anomalies such as session theft or unusual geo-logins, automated safeguards isolate the account. Access by NiamonX staff is allowed only via company-signed VPN endpoints and trusted hardware keys.
User information transmitted during registration or account management is protected through Application-Level Encryption (AES-256-GCM → Envelope Encryption → KMS → HSM). Additionally, Transparent Data Encryption (TDE) secures storage at the database layer, anonymizing all PII. API keys are hashed with SHA-256 and never retrievable. If processing is delegated to third-party services, data is anonymized, cryptographically signed, and transmitted only under secure protocols with user consent. Zero-log policy, your requests are stored locally in your browser.
All employee actions are logged and analyzed in real time by local AI security models. Access rights are restricted by department and operational scope. Anomalous activities within HelpDesk or administrative panels trigger immediate access suspension until verified. Servers are constantly monitored, and any irregular interaction is treated as a potential privacy breach — the node or cluster is isolated pending investigation. Staff only view minimal, anonymized operational data necessary to perform support duties.
All sensitive or breach-related datasets are encrypted at the application field level using AES-256-GCM with unique IV/nonce pairs. The system employs envelope encryption — each DEK (Data Encryption Key) is itself encrypted by a KEK stored in a dedicated KMS/HSM. Keys are rotated regularly and never co-located with data. Developers and operators have no access to raw PII or cryptographic material. For critical operations, Confidential Computing environments are used to ensure in-memory protection and full isolation. Data received from partners undergoes anonymization and integrity signing before being delivered directly to the client — bypassing all transit servers.
We provide actionable intelligence, real-time monitoring, and AI-powered analysis — turning massive data into insights that protect, inform, and scale with your operations.
Continuous detection of leaks, phishing campaigns, and compromised credentials to keep you one step ahead.
Visualize hundreds of thousands of WiFi points with passwords, MAC addresses, and geolocation for security audits.
Turn raw data from breaches, domains, and social networks into actionable insights with explainable AI.
Automated search robot scans infostealers and dark web leaks 24/7, alerting you to exposed data instantly.

We gather and analyze public and dark web data to uncover leaked credentials, vulnerabilities, and exposed assets linked to your organization.

Our AI agents process and correlate data across multiple sources, highlighting potential risks and producing real-time threat intelligence reports.

We integrate intelligent defense systems — OSINT bots, anomaly detectors, and alerting pipelines — to automate risk mitigation and response.

Our monitoring network tracks new breaches, infostealer logs, and darknet movements — keeping your digital identity protected at all times.
From individual analysts to enterprise-scale security teams — NiamonX offers flexible plans designed for every level of intelligence, automation, and protection.
Essential intelligence tools for individuals, analysts, or small teams starting their OSINT journey.
Perfect for investigative journalists, cybersecurity specialists, and small organizations that require deeper intelligence coverage.
Advanced threat intelligence, enterprise-grade customization, and full access to the entire NiamonX ecosystem.
From breach intelligence to OSINT automation — NiamonX empowers professionals to discover, correlate, and protect data faster than ever.


"NiamonX became our primary data-leak intelligence source. The PBS and ULP modules helped us identify compromised employee credentials across thousands of records in minutes — something that took hours before."


"The OSINT Tools suite is incredibly well-designed. We use the Visual OSINT and Brand Reputation modules daily — the accuracy and response speed easily surpass anything on the market."


"We integrated the NiamonX API into our internal monitoring dashboard. The combination of IP Intelligence and CorpData datasets provides unmatched visibility for threat correlation and entity tracking."
These are some of the most important questions our users ask. The full, detailed FAQ is available in your NiamonX Dashboard.
All authentication and identity management are handled through Zitadel IAM hosted in Reykjavík, Iceland. Your data is encrypted using AES-256-GCM and secured by Zitadel's Storage Encryption Layer — protecting passwords (Argon2id/bcrypt), OAuth secrets, refresh tokens, and private keys. Additionally, we enforce 2FA, password rotation, and behavioral anomaly detection to block suspicious logins and cookie theft.
We use a combination of Application-Level Encryption (AES-256-GCM with Envelope Encryption) and Transparent Data Encryption (TDE). Sensitive user data is stored as encrypted binary blocks, and decrypted only when accessed by authorized application logic. All API keys are hashed with SHA-256, backups are stored offline in isolated environments, and key management is handled by KMS + HSM for maximum security.
Access to user information is strictly limited to authorized team members under their assigned departments. Every action is logged and monitored by AI-driven anomaly detection systems. In the event of suspicious behavior, the affected account and internal session are instantly suspended pending investigation. Our principle is simple — minimal access, maximum privacy.
Public breach archives are encrypted at the field level using AES-256-GCM before being stored. Every data encryption key (DEK) is wrapped by a key encryption key (KEK) inside our HSM-based KMS. We rotate keys regularly, isolate workloads with Confidential Computing, and never store master keys alongside data. Partner-provided data is anonymized and cryptographically signed to maintain integrity and confidentiality.
Whether you're a business seeking data-driven insights or a security team ready to enhance your digital defense — NiamonX provides tools to analyze, automate, and protect. Need help integrating our AI solutions into your workflow? Reach out, and our team will guide you step-by-step.
Across enterprises in cybersecurity, data analytics, and automation fields.
Trusted by analysts, engineers, and business leaders worldwide.